I stumbled upon something neat I thought I’d share with you all while playing around with a demo of Internet Evidence Finder by Magnet Forensics. It is essentially using a memory image to determine where an individual may have been based on his/her geolocation queries, crowd sourced GPS check-ins (using Google Maps), etc. by analyzing Google Map tiles. Obviously, although IEF is known in the forensics community, I was impressed when using it for the first time.
I allowed IEF to carve web browser artifacts, chat sessions and Google map tile artifacts from a memory image (acquired via FTKi). Then had IEF map the coordinates from the tile file names and plot them across a world map (it is as simple as hitting “World Map” in the Report Viewer). You can also use Magnet’s free standalone GMTI (Google Maps Tile Investigator) to plot specified coordinates if you’ve pulled the artifacts using another method.
Although this is a known feature of the software, I found it incredibly impressive very useful. That you can do this directly from a memory image – with the same amount of success as from a hard drive image – is pretty cool.
Using that information you can get a general sense of where an individual was by what map information he or she searched for using Google Maps.
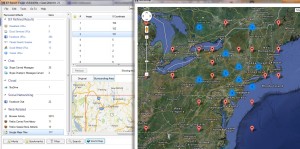
You can begin to develop a hypothesis as to the location’s significance when you compare this information to other known facts within your investigation. Knowing this information can help you weigh the importance of a cluster of plots and determine whether they are significant.
Instructions and more information on Google Map tile forensics is available in a great post by Magnet on their blog: http://www.magnetforensics.com/investigating-google-maps-how-the-tiles-tell-all/
For more information on Magnet’s IEF see: http://www.magnetforensics.com/products/internet-evidence-finder/
Information on the standalone (free) GMTI can be found at this address: http://www.magnetforensics.com/google-maps-tile-investigator/